It would be rather surprising if you haven’t heard of the Act to modernize legislative provisions as regards the protection of personal information (more commonly known as Bill 64, now Law 25), which was assented to by the National Assembly in September 2021.
With this legal reform, Quebec became the first province in Canada to adapt its strategies for protecting personal information to current technologies. Canada should soon follow suit, as it has recently tabled Bill C-27 to that effect.
As of September 22, 2022, your business must comply with the new legal obligations set out in Law 25. Failure to comply will expose you to major financial penalties, up to a maximum of $25 million, or 4% of your global turnover.
In my opinion, this reform was necessary. Many businesses manage personal data related to their employees, clients, and partners without really bothering to protect it properly.
Law 25 introduces new requirements, which will come into force gradually over three years. The first requirements must be met by September 22, 2022. Additional requirements will be effective as of September 22, 2023, and 2024. They will apply to all private businesses that collect personal information.
Throughout this article, I will suggest some steps you can take to ensure your business complies with the first set of requirements, avoids penalties, and, above all, adequately protects the data of the people who put their trust in you.
Have you named a privacy officer yet?
As of September 22, 2022, you must have formally named a privacy officer and established their role and responsibilities.
This person should know the type of personal information your business gathers, manages, and transmits. They should also know who is granted access to this information, and for what purposes.
Additionally, the privacy officer will be in charge of developing and implementing policies and measures related to the governance of personal information, such as rules on storing and destroying data, and on centralizing sensitive data to better monitor and protect it.
Have you determined what constitutes a confidentiality incident?
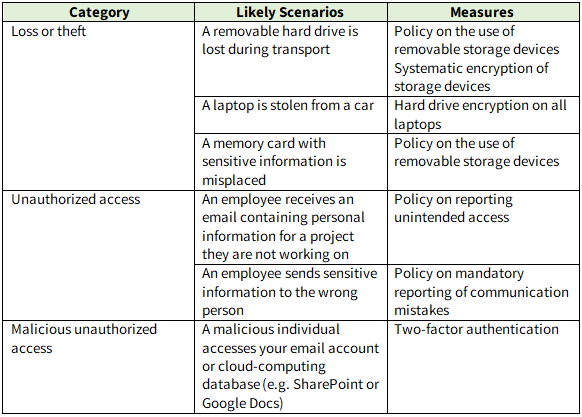
Think of potential scenarios in which your business’s data could be stolen or lost. The table below is an example of a simple method to determine potential incidents, the corresponding measures that could reduce the odds of those incidents occurring, and their impacts on your business, employees, clients, and partners.
Are you able to detect confidentiality incidents?
The law requires you to maintain a register of confidentiality incidents To maintain a register, you must first be able to detect the incidents in question. Here are a few pointers:
Encourage your employees to immediately report any access they might have to personal information that does not concern them. A simple email box (e.g. dangerous_access@yourbusiness.ca) and a rewards program could do wonders.
Determine specific locations in which to store sensitive information, and avoid making copies of the data or sending such information by email. Encourage employees to report any sensitive information found in other locations.
If possible, purchase a cybersecurity incident detection and response system. These types of services are more affordable than you may think. Make sure the service provider will detect incidents, handle remediation, and regularly keep you informed of incidents, including confidentiality breaches.
Take detailed notes on each incident in your register to show you have adequately analyzed it and that your response minimized the consequences of the incident.
Are you ready to react in the event of an incident?
Preparing for incidents is key to a successful response. Despite all your efforts, your business might experience a cybersecurity incident involving personal information. The worst thing you could do would be to pretend it never happened.
Set up procedures indicating the steps to follow to respond quickly to incidents. Your ability to demonstrate you acted promptly after an incident could be a mitigating factor if you were to be punished for failing to comply with your legal obligations.
Are you aware of your obligation to disclose an incident?
By law, you must report an incident to the Commission d’accès à l’information as well as to the people affected by the breach if the incident might cause serious harm to the victims. This means that you need a method to determine the severity of confidentiality incidents.
For instance, if an employee sends a quote for a project containing personal information to the wrong client, has serious harm been done? Who determines the severity of the incident, and how and when?
I recommend establishing a severity scale, based on parameters such as the volume of compromised sensitive information, the nature of the compromised information, and the people involved in the incident. This evaluation method allows you to demonstrate that each incident has been thoroughly analysed.
After analysis, if you conclude the incident must be disclosed, you must decide how to proceed and who will do it. To avoid litigation, the incident cannot be interpreted as having been caused by negligence.
If you have taken out cybersecurity insurance, your insurer may recommend the services of a breach coach; otherwise, your cybersecurity service provider may, along with your legal advisors, guide you through the situation.
Being proactive is the name of the game
Unfortunately, too many businesses wait to fall prey to a cyberattack or for an incident to occur before taking action. And they all say the same thing: “We should have been more proactive.” How might one do that, exactly? There’s no one-size-fits-all solution.
I suggest starting by answering the five questions asked in this article and seeing where your business is at. Make a plan and set it in motion. If you don’t have all the qualified resources internally, seek a partner.
Finally, never forget the importance of being prepared. The more detailed your incident response plan is, and the more your employees know to follow it to a T, (whether through training or incident simulation exercises), the better positioned your company will be to control a situation and limit the potential harm in the event of a real incident.
Being prepared will make it easy to prove that you took all the appropriate measures to protect the personal information in your possession and that you managed the incident diligently.
*This article was written in collaboration with Me Ariane Ohl-Berthiaume, Head of Legal Affairs at Mondata.


